Cybersecurity is serious business; an ever-present threat that executives are right to worry about and wonder how to guide. But understanding cybersecurity — and the steps your business should take to be more secure — is complex and technical. And let’s be honest, not very interesting for most people). Unfortunately, many of the resources out […]
This guide breaks down three important cybersecurity considerations. Most organizations make cybersecurity overly complicated because “you should do it either way.” This is not a valid argument. Business owners have tons of “have to” being thrown at them every day. It’s extremely difficult to cut through the fluff and identify what is critical and what […]
It’s true: even businesses that have impressive cybersecurity practices in place get breached. However, it is SIGNIFICANTLY less likely. The vast majority of breaches come from businesses that are missing common sense cybersecurity. It’s easy to blame the IT company for this. “I don’t know anything about cybersecurity, and I rely on my IT team […]
Cybersecurity can seem overwhelming at times. Your IT Provider handles this so why do you have to know things like why MFA is important? Our goal is to limit the impact any one cybersecurity layer has on our clients. However, in some situations it does require buy-in from our client base. Multi-Factor Authentication (MFA) is […]
There is a shift happening in the marketplace where businesses are increasingly choosing to outsource part of their IT to Managed Service Providers. For many larger businesses, it is not effective to keep all IT roles in house, or there isn’t enough budget for projects and people. So, IT managers choose co-managed IT. After 150+ […]
In the past, businesses either had an internal IT person/team or they worked with an outsourced IT company that provided Break/Fix or Managed IT Services. As the model has developed, businesses are finding it advantageous to have a combination of in-house and outsourced IT. For instance, they may not have the budget or need for […]
Microsoft 365 VS Google Workspace
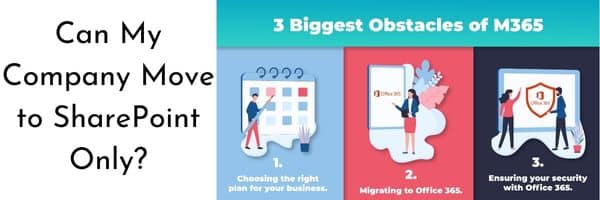
Most companies have had at least one server on their network. The network servers’ main purpose in life is to authenticate users, store files, send print jobs to the printers, and handle some security measures. All that is great stuff. But the real question is, can my company move to SharePoint only from having a […]
I’m sure you’ll agree with me when I say most people get an email in, skim it, and then maybe delete it. Most often that email sits in the inbox or gets filed in a folder so it is out of sight and out of mind, never to see any action again. Your information becomes […]
In part 1 of this article, IT Plans, Assessments, and Asset Management we learned about IT Plans and Strategy. If you haven’t read that yet, go back and give it a read. It will help to have that information before we talk about IT budgets and asset management. How do IT leaders forecast and budget […]